Threats to the security of your data and your networks are on the rise. One of the most commonly used methods is the Distributed-Denial-of-Service (DDoS) attack. According to the most recent research DDoS attacks have increased in their size and complexity in recent years.
What follows is a real life example of how an application level DDoS attack was followed by a DNS amplification attack and how it was stopped. This was against a customer using one of iomart’s shared hosting servers.
The attack starts
The attack began one mid-week morning. It started off small – several hundred Mbps of targeted traffic which would barely register on many monitoring graphs.
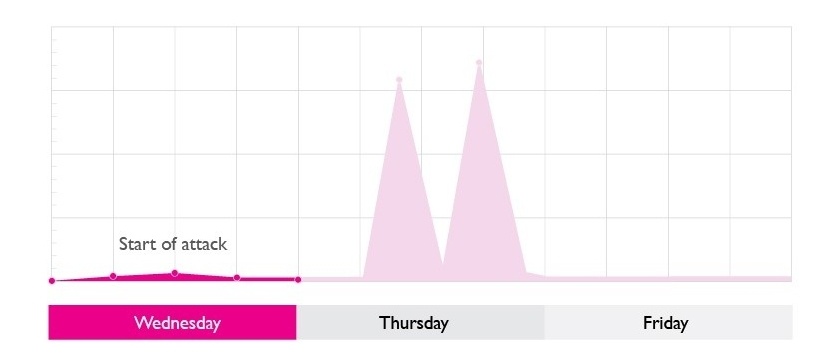
However our network DDoS protection services picked up immediately that something wasn’t quite right and started what’s called the auto-mitigation phase. This is something provided through our standard DDoS protection service.
As the attack continued it started to affect some of the other websites hosted on the server. We applied a range of other protection mechanisms, such as fine tuning where we allowed traffic from and what ports we were willing to accept traffic on to try to stop the degradation to the hosting platform.
Once the initial surge was dealt with, we then applied additional countermeasures and tweaked what we call ‘the rulesets’ further. Without those additional rulesets the attack would have been catastrophic.
The attack scales
If you look at the attack graph below, there’s a momentary gap on the Wednesday evening. This is probably where our infuriated attackers were scratching their heads trying to understand why this much traffic wasn’t taking down the target website. But they were determined, so on Thursday they threw the kitchen sink at us.
The attack was now eight times the original size, going from a couple of hundred Mbps to multiple Gbps. In the normal course of events it would take the very best enterprise equipment, deployed on a massive scale, to deal with this sort of attack. Certainly it would be well beyond the reasonable levels of the hardware deployed by most businesses.
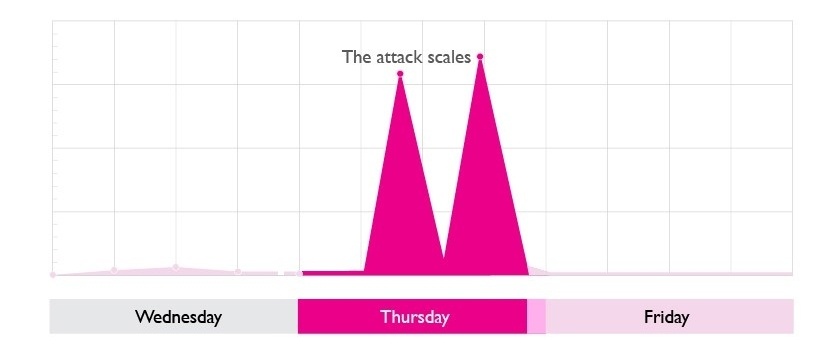
But our DDoS protection service was able to cope. It disposed of or ‘binned’ the attack traffic coming through our edge transit. We weren’t just stopping the attack at this stage, we were also gathering data so we could be sure we were binning the ‘bad’ traffic and not the good. At this point we then moved the blocking and filtering upstream to our core routers.
The attack stops
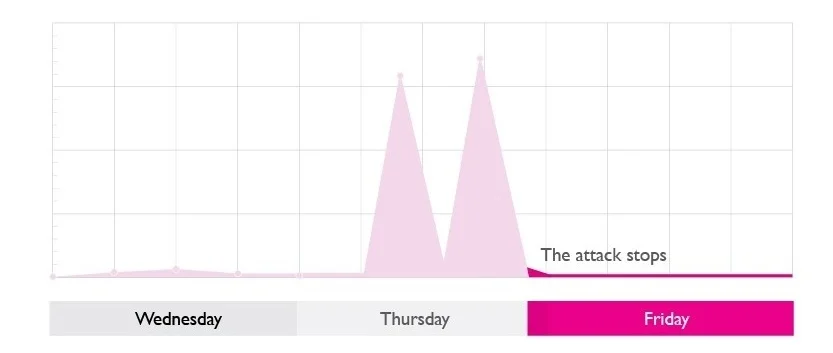
By moving upstream the attack on our customer’s websites effectively stopped. This is because the traffic was no longer being mitigated by our DDoS protection but was instead being killed by our core routers.
The combination of our core routers and DDoS protection meant we had tuned our response to the attack so finely that we were able to stop huge amounts of traffic from a real brute force attack.
The customer being targeted had been able to operate their online services during the attack without disruption.
